Zero Trust Architecture
Zero trust explicitly identifies users and grants them just the right amount of access. Businesses adopt zero trust architectures so that they can operate with reduced risks.
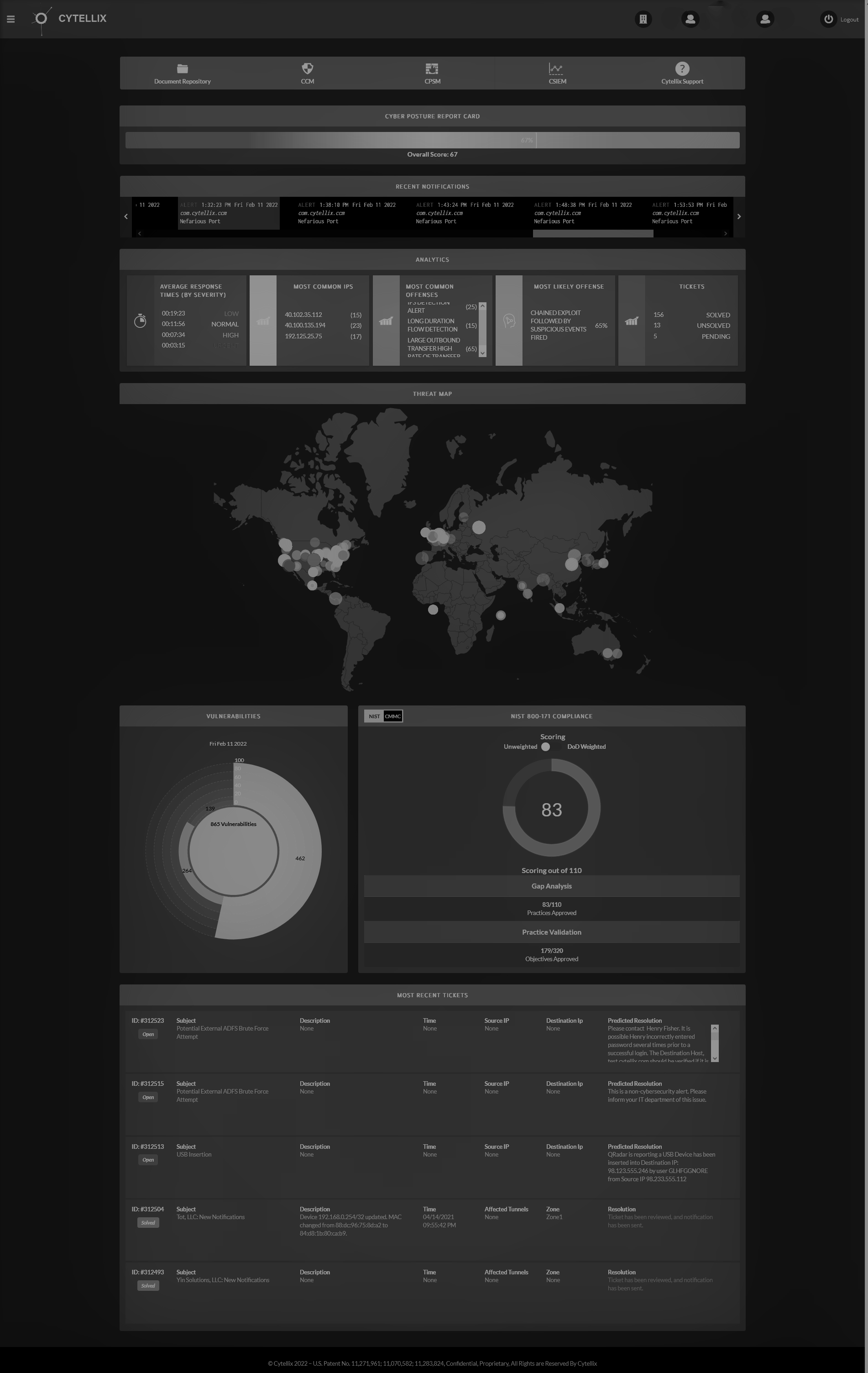
The CCWP leverages the zero-trust architecture by eliminating implicit trust and least access policies. Granular access policies with strong authentication secure users or applications to enable visibility to only what is needed. Applications components are secured and not implicitly trusted in their communication as well as logged and monitored for validation. The Cytellix® C-CWP™ zero trust architecture secures each organizations data by isolation and segmentation preventing lateral movement with "trust but verify" approach.
Defining Zero Trust
- Establish the Right Trust by defining the business operations being impacted, those where risk and exposure would be detrimental and where mitigation of risk is an imperative.
- Assume Compromise by building for resilience, prevention of breech with through detection and response capabilities.
- Use Identity and Context that is independent of actual location, location of data and works in any working environment.
Zero Trust Support in Cytellix Cybersecurity Platforms (C-CWP™)
Adaptive Security
Access should be granted and provided for each level of the organization at a level that enables them to do their job. As the job role requires access that increases risk, then monitoring in real-time is needed to adapt to changes.
Zero Trust and Cybersecurity
Zero Trust helps optimize a complete cybersecurity program. Using products and services that have a Zero Trust Architecture will bring value to the overall security posture of your organization
Security Framework Support
Zero Trust is being adopted by the security frameworks such as CMMC, NIST, ISO and others. This shift in frameworks to recommended or require Zero trust will impact Security Compliance.
Impact on Business Leaders
Business leaders, BOD's and Executives need to consider impacts of Zero Trust on their business process and regulatory compliance for cybersecurity.
Impacted Markets
Highly regulated industries such as supply chains in DoD, Medical Technology, Pharmaceuticals, Automotive and Financial services, Insurance and Technology need to consider enablement as a standard.
Security As a Solution
As Cybersecurity becomes a key business strategy for most organization, key initiatives will drive adoption of security as a service. Support for Zero Trust in: GRC, MDR, XDR and EDR is required and must be resilient to threats.
Action
To learn more, contact us to speak to a Cytellix® Subject Matter Expert (SME) able to answer your questions, and arrange an demonstration at your convenience.