CMMC 2.0: Here’s Everything You Need To Know
Newly released CMMC 2.0 Makes Changes and Creates More Uncertainty of What to Do Next?
Before we start with the background and changes, let’s talk about the "Big Elephant” in the room. Clearly, the compliance and certification process developed by the DoD and the non-profit organization liaisons has been mishandled. I am being polite here, and not intending to insult anyone directly however, this does highlight the movie comedy and colloquial meaning of Groundhog Day. Since the Library of Congress selected the film for preservation in the National Film Registry, I found the humor not cynicism. We have seen the start and restart of the cyber programs for DoD for the past 5-years, what makes this different?
Opinion: This is different and the information we have in the DoD supply chain must be protected from our adversaries. This is a serious issue and needs clear and precise guidelines as the supply chain will not spend money on protection of the information that protects national security, unless they must. That’s an unfortunate reality.
The DoD announced a change to CMMC 1.0 and renaming as CMMC 2.0. Within this change are a host of enhancement and implications for the supply base at a high level. I will outline the changes as directly as possible. The main change is the addition of self-assessment similarly to NIST 800-171 under DFAR 252.204-7012. In addition to the self-assessment is the requirement for annual affirmation by the company leadership. This is where the rubber really hits the road. Affirmation under the
False Claims Act, where both prosecution and insider complaints will be addressed. I suggest all suppliers read this link. In addition to these, changes in 2.0 will be lower costs for suppliers as certification by a 3rd party is no longer required in many cases.
There is now the ability to present interim status vs 100% compliance as we have with the current DFARS and NIST requirements. These interim reports can be handled in the traditional manner by presenting a Plan of Action and Milestones (POAM) that have a less than 180-day completion date for allowed baseline gaps. Unallowed gaps will have a “No POAM” designation and need to be implemented. If you have any doubts, work with a highly skilled 3rd party who has expertise in these standards and track record of enabling comprehensive successful standards-based cyber programs. The information presented by the suppliers in POAM’s or claiming 100% compliance will be evaluated and can and will likely trigger audits if certain high level cyber controls are not met or the 100% compliance score creates suspicion of a false claim. Be careful to present accurate and validated information.
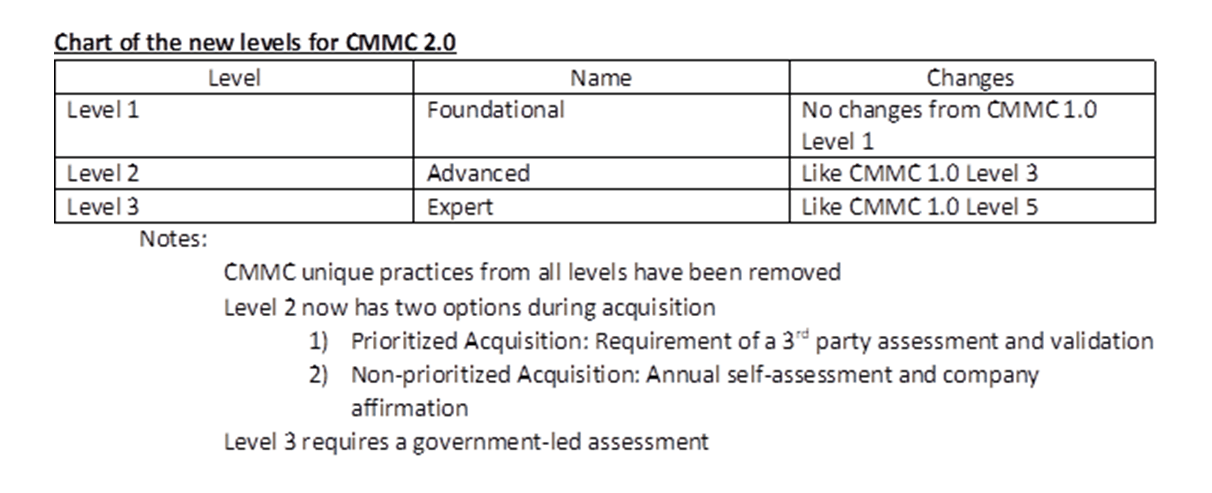
There will be a rulemaking process that is expected to take place for 9+ months and the CMMC 2.0 will not show up in acquisitions until the rulemaking process is complete. There is an expectation that once the rulemaking is complete, the effects of and implementation will likely be swift and mandatory.
So, what does this all mean? Reality, if you are a DoD supplier or have plans to be one.
YOU MUST be compliant with the DFARS clause 252.204.7012 and NIST 800-171 under your current contracts. (NIST SP 800-171 & CMMC Interim Rule Effective November 30, 2020 - Cytellix).The False Claims Act applies today to all cyber compliance representations. You should start now preparing for CMMC 2.0 as it clearly aligns with DFARS and NIST. Waiting is a bad idea. Why you ask? It is very clear that most suppliers and Small and Medium Businesses are not cyber prepared and nowhere near compliance with any cyber framework. The timeframe for a typical business to understand, develop and implement full compliance is more than 1-year assuming they have skills and personnel to complete the objectives.
*If you have any questions, please reach out to our experts – [email protected]