A Closer Look At CMMC & NIST 800-171 Preparedness

We all know that regulated Federal Government information is safeguarded to prevent cyber-attacks from the adversaries of the United States, but did you know that any and all sensitive data, government-owned or not, must be protected by adhering to a specific set of rules? Controlled Unclassified Information (CUI) is information that is sensitive and relevant to the national security interests of the United States, but not under strict Federal regulation. According to the National Archives and Records Administration, the Executive Agent is responsible for creating and implementing unclassified data standards and overseeing compliance. CUI is considered any potentially sensitive, unclassified data that require controls in place to define its proper safeguarding or dissemination. What is NIST 800-171, and how can you meet the requirements? Let's take a look!
What is NIST 800-171?
NIST is the acronym for National Institute of Standards and Technology, and 800-171 is a specific publication. NIST 800-171 governs Controlled Unclassified Information in Non-Federal Information Systems. Essentially, 800-171 is a list of standards that must be met to adequately safeguard and distribute personal or sensitive information that is not officially classified. NIST 800-171 was first created in 2003, shortly after the Federal Information Security Management Act was passed. Following a series of serious cyberattacks, it became clear that cybersecurity needed to be ramped up. NIST regulations have changed slightly since the beginning, particularly for certain government agencies like NASA, the Department of Defense (DoD), and the General Services Administration (GSA). Commercial supply chain organizations are also required to adhere to these new guidelines.
- All contractors awarded contracts to provide products or services that require the use of Controlled Unclassified Information (CUI) is ordered to comply with DFARS 252.204-7012
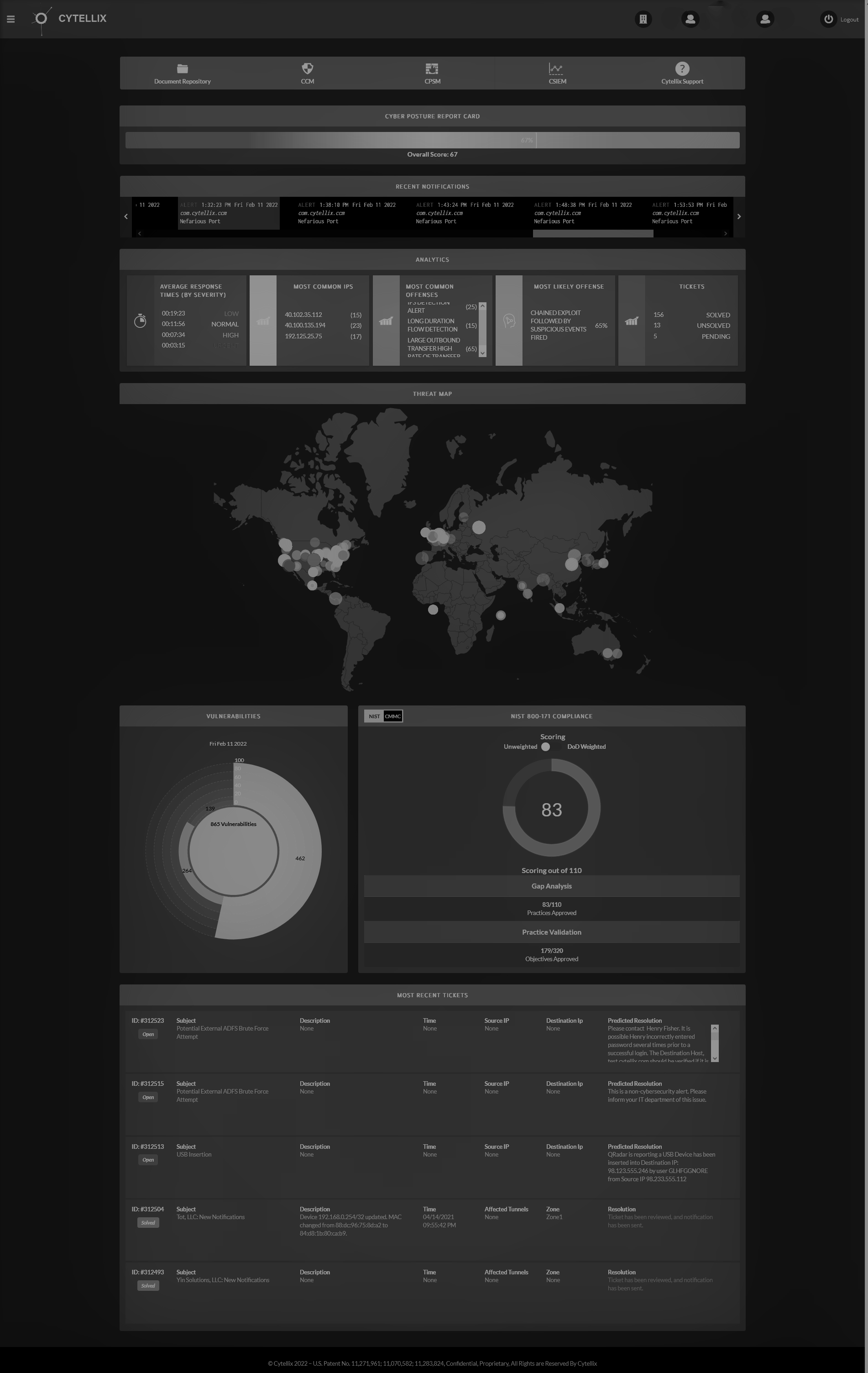
- Over 100 controls must now be addressed, as well as the cybersecurity posture of the supplier’s network or system across the 14 security domains defined in NIST SP 800-171
- The obligation of proof is now placed on the supplier and their entire supply chain.
- Failure to comply will result in a Corrective Action Report (CAR), loss of contract, or potential legal actions.
NIST 800-171 was designed to get all companies on the same set of guidelines for cybersecurity. Prior to the publication, each company could make its own rules. When everyone operates differently, there is no uniformity, and each company will have weak points that are easy to attack. By regulating the process, the government is now confident that sensitive data is under lock and key.
What is CMMC?
The Cybersecurity Maturity Model Certification is part two of NIST 800-171. CMMC is a program initiated by the United States Department of Defense (DoD) in order to measure their defense contractors’ capabilities, readiness, and sophistication in the area of cybersecurity. The guidelines set forward in NIST 800-171 are the baseline for CMMC. Using CMMC, it can easily be determined precisely how prepared a company is. There are five levels in total, with Level 1 being baseline NIST requirements and Level 5 being highly advanced with custom processes and cyber technology that is constantly working. As of September 2020, the Department of Defense (DoD) began requesting information that contains CMMC specifications. It is clear that they have a timeline for getting the CMMC into all contracts by 2026. At the moment, CMMC applies to Department of Defense prime contractors and subcontractors. The ultimate goal is to have it apply to each and every contract that handles any sensitive information.
How Can Cytellix Help?
It can be daunting for companies and contractors to figure out how compliant they are to these regulations. Cytellix works with several government agencies, including the Department of Defense (DoD), so our team knows the guidelines like the back of our hands. We offer a collection of services that will check off the necessary boxes. We create and implement cybersecurity solutions that will help you meet the expectations of these relatively-new guidelines. We'll check out your current situation, find your weak spots, and propose solutions to build up your security systems. The more cybersecurity you can implement now, the more prepared you will be as the DoD cracks down on NIST 800-171 now and CMMC in the near future. It's far easier to be prepared early than to play catch up when the new contracts come out. By working with our team, you will have a personalized package that can grow and change as you do. It's expected for more versions of CMMC to be released prior to its complete implementation, and Cytellix will be there to make sure you stay on track. Cytellix is available to provide a detailed security services assessment. Our goal is to ensure you are fully aware of the steps required to remain compliant, cyber prepared for certification, and provide a plan of action that will minimize time or cost disruption.
The concept of NIST 800-171 and CMMC can be a bit challenging to grasp. The key takeaway is that the Department of Defense (DoD) is putting regulations in place to strengthen security surrounding sensitive but unclassified data. This will protect contractors, companies, and consumers from cyber-attack, and it will keep information away from hackers inside and outside of the US. Preparing for CMMC can be tricky, but Cytellix is here to help. Learn more about our NIST 800-171/CMMC services at
https://bsyl.ink/NIST800-171. If you're ready to increase your cybersecurity and become more compliant with these guidelines, call us at (949) 215-8889. We look forward to hearing from you!
Cytellix has expert capabilities in cybersecurity technology, risk management frameworks (RMF, NIST, CMMC, GDPR, FFIEC, ISO) and provides a complete visibility platform that supports: DoD customers, DIB Customers, DoD Supply Chain, and other highly regulated industries (Finance, Automotive, Utilities, State and Local Government). Our technology stack includes SIEM as Service, 24x7 SOC, Vulnerability Management, Real-time continuous cyber monitoring, Firewall Management, and threat hunting and threat correlation.
The post A Closer Look At CMMC & NIST 800-171 Preparedness appeared first on Cytellix.